What Is a GRC Framework? How to Build One for Cyber Security
Need a GRC framework for cyber security management? This 5-step guide for leaders explains the 3 pillars (Governance, Risk, Compliance). Get your plan.
Cyber security management, a governance risk and compliance framework is a mouthful. It's a long winded, corporate speak monstrosity of a term.
But it’s also the single most important strategic concept you, as a business leader, will (or won't) wrestle with this decade.
You are probably here because you feel the chaos. Your CISO is asking for a new million dollar tool. Your legal counsel is terrified about GDPR or CCPA fines. Your finance department just sees a ballooning IT budget. And your biggest client is sending you a 50 page security questionnaire that must be passed.
Everyone is screaming. Everyone is spending. But nobody is aligned.
This is the problem. A GRC framework is the solution.
It is not another tool. It is not another line item. It is the strategic model you use to get all those warring factions, your CISO, your CFO, your legal team to speak the same language. It's the blueprint that aligns your entire security program with your actual, money making business goals.
Most companies run their security like a volunteer fire department. They buy alarms, they buy a truck, and they wait for a fire. Then they run around in a panic.
A GRC model is the opposite. It’s the city planner, the architect, and the fire marshal all in one. It prevents the fire. And if a fire does start, the plan is already in place. This is what real cybersecurity compliance solutions are built for..
Deconstructing Cyber GRC : What It Means for Management
GRC stands for Governance, Risk, and Compliance.
You have to stop thinking of these as three separate topics. They are not. They are three legs of the same stool. Without one, the entire thing collapses.
The old way (and the wrong way):
-
Your legal team handles Compliance.
-
Your IT team handles Risk (sort of).
-
Your board handles Governance (maybe).
The result? Silos. Waste. Gaps. The legal team buys a compliance tool that IT can't stand. The IT team buys a risk tool that doesn't actually prove compliance. And the board just sees red on a balance sheet.
GRC is the strategic antidote. It's the integrated model for managing all three in one coordinated effort. It's the Rosetta Stone that translates technical vulnerabilities into quarterly business impact for the board.
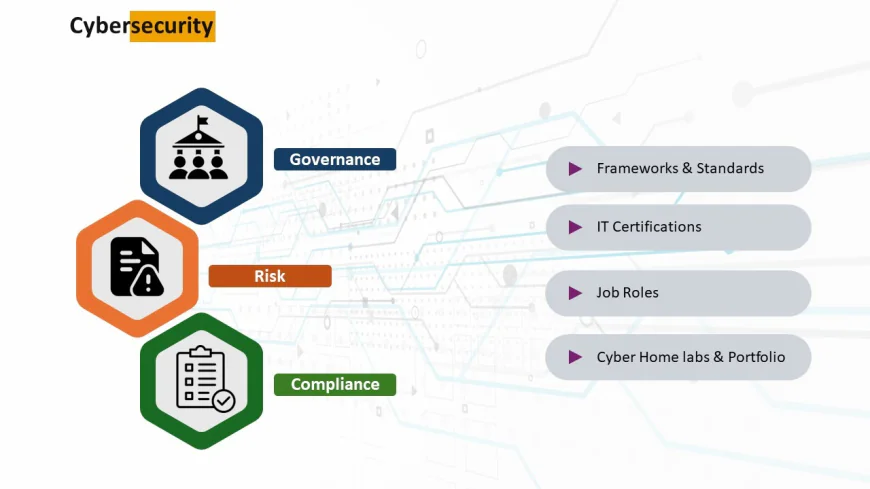
The 3 Pillars of a Cybersecurity GRC Framework
I’ve seen dozens of companies fail because they only focus on one pillar. You can't. A GRC driven program balances all three.
Pillar 1: Governance (The G )
This is Who's in charge? pillar. It’s the most boring, and therefore the most critical, part.
Governance is the structure of accountability. It is the set of policies, rules, and frameworks your company chooses to live by to achieve its goals.
For a CXO, this isn't about firewall settings. It's about answering the big questions:
-
Who is accountable? If there's a breach, who actually owns that failure? The CISO? The CEO?
-
What are the rules? This is your internal policy management. Employees will not use personal devices for company data.
-
What is our risk appetite ? This is a term you must learn. It's the amount of risk your business is willing to accept. Are you a bank? Your appetite is zero. Are you a startup? You might accept more risk for the sake of speed. Governance defines this line.
Without good governance, you have anarchy. You have a dozen different departments buying a dozen different tools, all while pointing fingers at each other.
Pillar 2: Risk Management (The R )
What are the threats? pillar.
Risk management is the ongoing process of identifying, analyzing, and addressing cybersecurity threats.
This is where most IT led programs live. But they often do it wrong. They focus on technical risk, not business risk.
A true GRC based risk approach doesn't just list 1,000 vulnerabilities. It prioritizes them. It asks the real questions:
-
What are our crown jewels ? What data, if stolen, would kill our business?
-
What are the actual threats? (Not just hackers, but maybe a disgruntled employee or a clumsy partner).
-
What is the business impact? Who cares about a critical vulnerability on a test server? What about the medium vulnerability on your payment processor?
I’ve seen companies spend $500,000 to fix a $50,000 problem, all while ignoring a $5,000,000 problem. That is what happens when you manage risk without the G (Governance) to guide you. It's just panicked, technical whack a mole.
A mature cybersecurity risk management program is proactive. It hunts for threats, not just waits for alerts. It uses data to decide what to fix first, based on what matters to the business.
Pillar 3: Compliance (The C )
This is how we prove it? pillar.
Compliance is the act of following the rules, laws, and regulations that are forced upon you.
This is the or else part of the equation.
-
Or else you'll face massive GDPR fines.
-
Or else you'll fail your HIPAA audit.
-
Or else you'll be kicked out of the defense supply chain for failing CMMC.
-
Or else you'll lose your ability to process credit cards for failing PCI compliance.
Compliance is about adherence. It’s about generating the proof, the audit trails, the reports, the documentation that shows you are doing what you say you are doing.
The biggest mistake I see? Companies make compliance the goal. This is backwards.
When you chase compliance, you do the absolute minimum to pass the audit. You check the box. And you are almost always still insecure.
In a GRC model, compliance is the outcome. It's the natural result of having good Governance (you have the right policies) and good Risk Management (you fixed the real problems). You don't study for the test. You know the material is cold, so the test is just a formality.
Why GRC Is a Business Strategy, Not Just an IT Project
This is the part that you, as a leader, need to internalize. When I talk to boards, this is the slide I spend the most time on.
Benefit 1: It Aligns Security with Business Goals
A GRC framework forces a simple question for every security related decision: Does this help the business? This simple question stops the CISO from buying a cool new tool and forces them to justify the business case. It ensures security spending (a cost center) directly supports business growth (a profit center), for example by enabling you to win contracts that require SOC 2.
Benefit 2: It Provides a Single View of Risk
GRC breaks down silos. Instead of getting three different, conflicting reports from IT, Legal, and Audit, GRC integrates them. It provides a single, unified dashboard for the board that shows the total risk posture of the company. This is the only way you can make an intelligent, informed decision.
Benefit 3: It Slashes Costs and Increases Efficiency
Silos are expensive. When you don't have a GRC model, you have an incredible amount of duplicated effort. You have the IT team performing a risk assessment while the audit team performs a separate control audit. It's madness. A GRC framework identifies these overlaps. You control it once, and then you test it once. This single act saves hundreds of man hours and eliminates redundant, useless software.
Benefit 4: It Makes Your Decisions Defensible
This is a big one. When a breach does happen (and it will), the first question from regulators, lawyers, and your customers will be: What did you do to prevent this? If your answer is We had a GRC program, here's our risk appetite statement, here's our risk assessment, and here's the business decision we made... you are in a defensible position. If your answer is Uh... our IT guy bought a firewall... you are in a world of hurt.
How to Implement a Cybersecurity GRC Framework (A 5 Step Process)
This is not a one week project. This is a cultural shift. But it's a process, and it has steps.
Step 1: Define Governance & Get Leadership Buy In
Do not skip this. You, the CXO, must be the champion.
-
Action: Form a governance committee. This must include leaders from IT, Legal, Finance, HR, and Operations. This is not just an IT problem.
-
Action: Get the board to sign off on a risk appetite statement. This is your guiding star.
Step 2: Conduct a Unified Risk Assessment
You cannot manage what you do not measure.
-
Action: Identify your crown jewels. What data and systems are mission critical?
-
Action: Identify all the threats to those assets (insider, external, third party).
-
Action: Map these risks to the business. Don't just say High. Say, High risk of $3M in fines and 20% customer loss.
Step 3: Select & Map Your Control Frameworks
Don't reinvent the wheel. The playbooks are already written.
-
Action: Choose the frameworks that apply to you. This is your compliance part. You might be bound by PCI, HIPAA, or CMMC.
-
Action: For your overall security program, adopt a gold standard framework like the NIST Cybersecurity Framework (CSF). This is the playbook most mature organizations use. You should get expert NIST compliance services to guide this; it's not a DIY project.
-
Action: Perform a gap analysis. Compare your list of risks (Step 2) to the controls in your chosen framework (Step 3). The gaps are your to do list.
Step 4: Implement GRC Tools & Technology
After you have your strategy, then you can buy the tools.
-
Action: Look for GRC software. This is the platform that will automate all this. It's the central home for your policies (G), your risk register (R), and your audit evidence (C).
-
Action: The tool supports the process. It does not replace it. I've seen too many $250,000 GRC platforms become the world's most expensive spreadsheets because the company skipped Steps 1 3.
Step 5: Monitor, Audit, and Continuously Improve
GRC is not a one and done project. It's a program.
-
Action: Implement continuous monitoring. Your GRC platform should be pulling in data from your security tools (like your SIEM) in real time.
-
Action: Conduct regular internal audits. Test your own controls.
-
Action: Report back to the governance committee (Step 1). Show the new risks. Show the progress. Get new decisions. This is the loop that makes GRC a living, breathing part of your business.
-
Resource: For a simple, ground level example of controls, this CMMC Level 1 Compliance Checklist shows how basic controls form the building blocks of a framework.
Cybersecurity GRC Frameworks vs. GRC Strategy
Let's clear this up. These two terms are used interchangeably, and it causes huge confusion.
-
A GRC Framework is a published, off the shelf model. Think of it as a cookbook. NIST CSF, ISO 27001, and COSO are frameworks. They give you the ingredients and the steps.
-
Your GRC Strategy is your unique approach. It's what you're making for dinner. You use the NIST cookbook (the framework) to build your specific security program (the strategy) that protects your company (the dinner).
Your strategy adopts a framework. It does not equal it.
Cybersecurity GRC FAQs for Business Leaders
What is the difference between GRC and Integrated Risk Management (IRM)?
You'll hear analysts like Gartner talk about IRM. Honestly? It's mostly a re branding. The idea is that IRM is the evolution of GRC, focusing even more on linking risk directly to strategic business performance. For your purposes as a leader, the philosophy is the same: stop looking at risk in a silo.
Do I need to buy GRC software to have a GRC framework?
Absolutely not. Do not buy a tool first. I’ve seen this a dozen times and it fails every time. Your GRC program for the first year might just be a set of very well organized spreadsheets and a dedicated committee. That is infinitely better than a $100,000 tool that nobody understands or uses. Start with the process (G), not the platform.
We're a Small Business (SMB). This sounds like an overkill. Where do we start?
GRC is for you. It just scales. Your governance might just be you, the owner, setting the rules. Your risk assessment might be a 2 day engagement, not a 6 month one. Your compliance might just be PCI DSS. Don't try to boil the ocean.
-
Name one person who owns security.
-
List your 3-5 crown jewel assets.
-
Pay for a basic risk assessment.
-
Focus on the fundamentals (MFA, backups, patching). That is a GRC program. It's just a small one. The cost, like a CMMC compliance cost breakdown, scales with your complexity.
Stop Managing Chaos. Start Managing Risk.
A cyber security management governance risk and compliance framework is, at its heart, a machine for making good business decisions.
It’s the structured, logical, and defensible way to manage the digital chaos that all modern businesses face. It's the only way to stop wasting money, align your teams, and finally get a real, executive level answer to the question: Are we secure?
If you're still managing security like a chaotic fire department, it's time to hire an architect.
At Defend My Business, we are those architects. We don't just sell you a tool; we build the strategic GRC blueprint with you, starting with a clear eyed assessment that translates technical jargon into a business first action plan.










