Social Engineering Testing Services vs. Traditional Penetration Testing.
Uncover the advantages of social engineering testing versus traditional penetration testing. Strengthen your cybersecurity measures with informed choices.
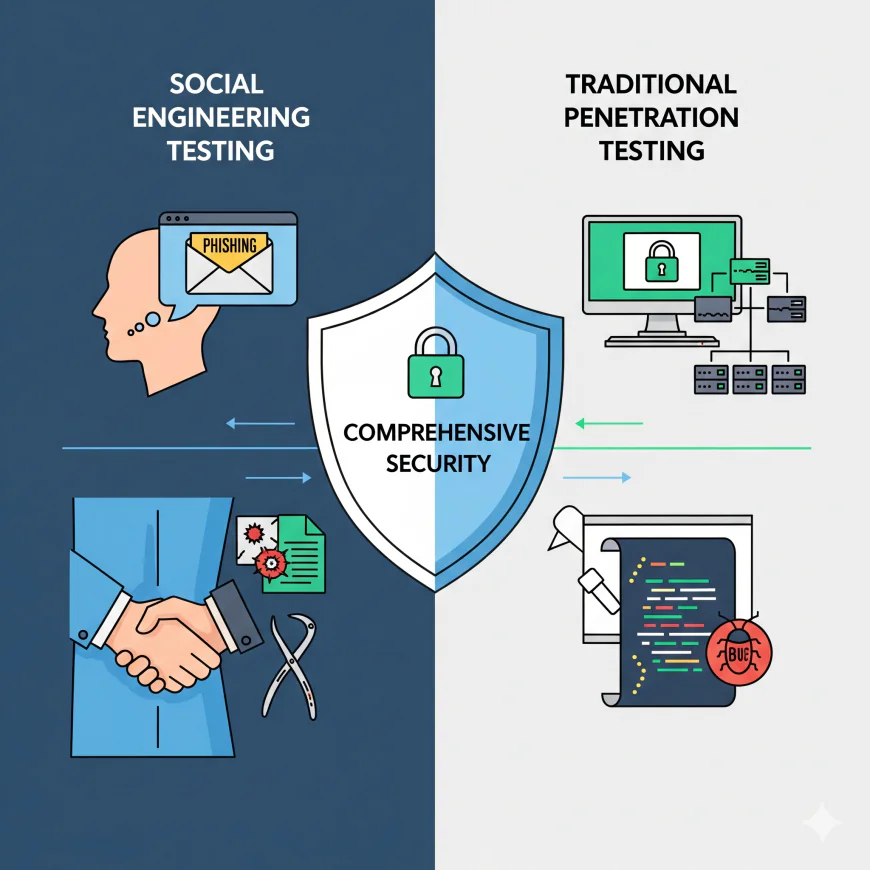
In today’s connected world, organizations face a growing number of cyber threats. While technical vulnerabilities remain a major focus, human behavior often becomes the weakest link. This is why Social Engineering Testing Services have emerged as a crucial component of modern security strategies. But how do these services compare to traditional penetration testing? Let’s break it down.
What Is Traditional Penetration Testing?
Traditional penetration testing focuses on identifying vulnerabilities in systems, networks, and applications. Ethical hackers simulate real-world cyberattacks to expose security flaws, from outdated software to misconfigured firewalls. By doing so, businesses gain valuable insights into their technical weaknesses and can patch them before real attackers exploit them.
Organizations that rely heavily on online operations — for example, those using Comcast Internet for Business to power their networks — especially benefit from regular penetration tests to ensure their infrastructure is secure. Combined with cybersecurity consulting services, penetration testing remains one of the best ways to identify and mitigate technical risks.
What Are Social Engineering Testing Services?
Unlike traditional penetration testing, which targets systems and applications, Social Engineering Testing Services focus on the human element of security. These tests simulate phishing emails, phone-based attacks (vishing), or physical intrusions to gauge how employees respond to real-life manipulation attempts.
By using these methods, businesses can determine whether their staff follows security policies, reports suspicious activities, and resists attempts at credential theft. The findings often guide security awareness training programs, making employees an active line of defense rather than a vulnerability.
Key Differences Between the Two
| Feature | Traditional Penetration Testing | Social Engineering Testing Services |
|---|---|---|
| Focus | Technical vulnerabilities in IT systems | Human vulnerabilities and behavior |
| Method | Scanning, exploiting, and reporting on network/app flaws | Phishing, vishing, pretexting, and physical security tests |
| Outcome | Patch software and infrastructure weaknesses | Improve employee awareness and response |
Why You Need Both
No single test can cover all aspects of security. While penetration testing strengthens your digital perimeter, social engineering testing strengthens your human firewall. Together, they provide a complete picture of your organization’s resilience against cyber threats.
When combined with ISO 27001 consultancy services, these tests also support compliance efforts. ISO 27001 emphasizes a risk-based approach to information security, and including human factors in your risk assessment can improve certification readiness.
Leveraging Technology and Software
Enterprises can also integrate tools such as enterprise telecom expense management software to gain a unified view of their communications infrastructure. This not only optimizes costs but also improves visibility into network usage — a crucial factor for spotting anomalies that could indicate a breach or insider threat.
Conclusion
The cybersecurity landscape is evolving rapidly. Organizations can no longer rely solely on traditional penetration testing to protect their assets. By adopting Social Engineering Testing Services alongside penetration tests, businesses can secure both their technology and their people. With the right mix of cybersecurity consulting services, ISO 27001 consultancy services, and secure infrastructure like Comcast Internet for Business, your organization can build a stronger, more resilient defense against today’s most sophisticated cyberattacks.










