Information Security Certificate for Data Protection
Information security certificate helps professionals protect data, build trust, and stay relevant as organizations prioritize security in a digital-first world.

Information security certificate helps professionals protect data, build trust, and stay relevant as organizations prioritize security in a digital-first world.
There’s a quiet shift happening in the professional world, one that most people don’t notice until it’s too late.
Companies aren’t just hiring for skills anymore.
They’re hiring for trust.
Every email you send, every system you access, and every customer record you touch carries risk. And organizations know this. Data breaches, ransomware attacks, and compliance failures don’t just cost money; they destroy reputations overnight.
That’s why information security has moved from the IT department to the boardroom agenda.
If you’ve ever wondered how to stay relevant, valuable, and respected in a digital-first world, an information security certificate might be the smartest decision you make for your career.
1. What Is an Information Security Certificate?
An information security certificate is a professional credential that validates your ability to protect data, systems, networks, and digital assets from threats, misuse, and unauthorized access.
But it’s more than just a certificate.
It proves that you understand:
-
How information is created, stored, and shared
-
Where security risks come from
-
How to prevent breaches before they happen
-
How organizations manage security, risk, and compliance
Unlike casual online courses, a professional information security certification follows structured frameworks used by real organizations across industries.
It tells employers, “This person knows how to safeguard what matters most.”
2. Who Can Do an Information Security Certification?
One of the biggest myths about information security is that it’s only for hardcore technical experts. That’s simply not true.
An information security certificate is ideal for:
IT & Technical Professionals: System administrators, Network engineers, Software developers, IT support specialists
Non-Technical Professionals: Risk and compliance officers, project managers, business analysts, auditors and consultants
Students & Career Switchers: Graduates exploring stable tech careers, Professionals transitioning from non-IT roles, Anyone seeking long-term career security
Managers & Decision-Makers: Team leads, Department heads, Business owners responsible for data
If your role involves data, systems, people, or decisions, information security already affects you even if it’s not in your job title.
3. What Will You Learn in an Information Security Certificate?
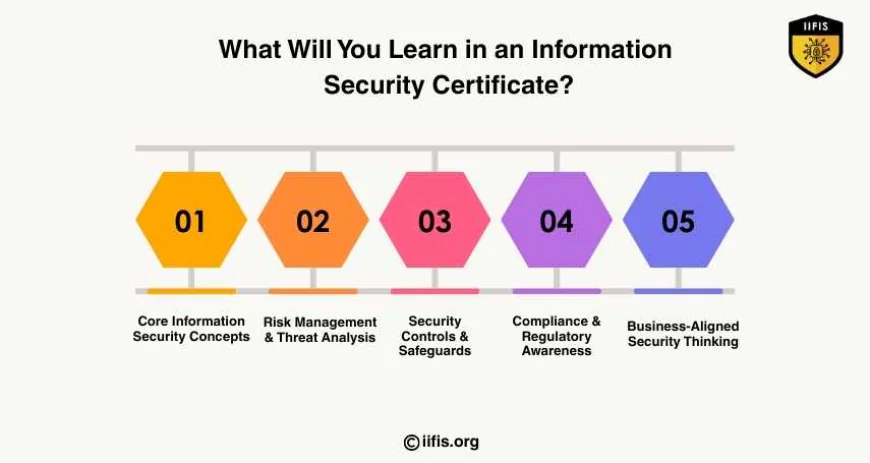
A well-designed information security certification focuses on practical understanding, not unnecessary complexity.
Here’s what learners typically gain:
Core Information Security Concepts
-
Confidentiality, Integrity, and Availability (CIA Triad)
-
Information classification and data handling
-
Security governance and policies
Risk Management & Threat Analysis
-
Identifying vulnerabilities
-
Assessing and prioritizing risks
-
Understanding internal and external threats
Security Controls & Safeguards
-
Administrative, technical, and physical controls
-
Access control and identity management
-
Incident response basics
Compliance & Regulatory Awareness
-
Understanding why compliance matters
-
Aligning security with organizational policies
-
Supporting audits and assessments
Business-Aligned Security Thinking
-
Communicating security risks to non-technical stakeholders
-
Balancing security with productivity
-
Making informed security decisions
The goal isn’t to turn you into a hacker; it’s to help you think like a security professional.
4. Tools and Technologies Used in Information Security Certification
While information security isn’t just about tools, understanding the ecosystem is critical.
Most certifications introduce learners to commonly used tools and technologies such as:
Security Tools & Concepts
-
Risk Assessment Frameworks: Structured methods used to identify, evaluate, and prioritize security risks within an organization.
-
Security Information and Event Management (SIEM) Concepts: Systems that collect and analyze security logs to detect threats and suspicious activities.
-
Identity and Access Management (IAM) Basics: Controls that ensure only authorized users can access systems, data, and applications.
Network & System Security Tools
-
Firewalls and Intrusion Detection Systems: Technologies that monitor and control network traffic to block unauthorized access and attacks.
-
Endpoint Security Solutions: Tools that protect individual devices like laptops and servers from malware and cyber threats.
-
Encryption and Authentication Mechanisms: Techniques that secure data and verify user identities to prevent unauthorized access.
Monitoring & Incident Response Tools
-
Log Analysis Platforms: Tools that review system and application logs to identify unusual or malicious behavior.
-
Threat Detection Methodologies: Approaches used to identify potential cyber threats before they cause damage.
-
Incident Reporting Workflows: Structured processes for documenting, escalating, and responding to security incidents effectively.
5. How Long Does an Information Security Certification Take?
One of the most common questions learners ask is about time commitment.
The answer depends on:
-
Your background
-
The certification level
-
Learning pace
Typical Timeframes
-
Beginner to Intermediate Certifications: 2–4 months
-
Advanced Certifications: 4–6 months
Most professionals complete certifications while working full-time, studying a few hours per week.
The key isn’t speed; it’s consistency. A structured program makes learning manageable, even with a busy schedule.
6. How IIFIS Helps People Learn Information Security
Learning information security can feel overwhelming, especially when resources are scattered or overly technical.
This is where IIFIS stands out.
What Makes IIFIS Different?
-
Beginner-Friendly Curriculum: Designed to simplify complex concepts without losing depth.
-
Industry-Relevant Content: Aligned with real organizational security needs, not outdated theory.
-
Structured Learning Path: Clear progression from fundamentals to applied knowledge.
-
Career-Oriented Approach: Focused on employability, confidence, and real-world application.
7. Career Opportunities After an Information Security Certificate
An information security certification opens doors across multiple roles and industries.
Common career paths include:
Entry to Mid-Level Roles
-
Information Security Analyst: Monitors systems, identifies security risks, and helps prevent data breaches through proactive controls and analysis.
-
Risk Analyst: Assesses potential security risks to the organization and recommends strategies to minimize business impact.
-
Security Operations Associate: Supports day-to-day security operations by monitoring alerts, responding to incidents, and maintaining security tools.
-
Compliance Analyst: Ensures the organization follows security policies, standards, and regulatory requirements through audits and documentation.
Advanced & Specialized Roles
-
Information Security Manager: Leads security strategy, manages teams, and ensures organizational data is protected at a strategic level.
-
Risk and Governance Consultant: Advises organizations on building strong security governance frameworks aligned with business and compliance goals.
-
Security Auditor: Reviews security controls, policies, and systems to ensure they meet internal standards and external regulations.
-
Cybersecurity Advisor: Provides expert guidance on security risks, threat mitigation, and long-term cybersecurity planning.
8. Industries Where Information Security Professionals Work
Information security isn’t limited to tech companies.
Professionals are in demand across:
Banking and Financial Services: Protect sensitive financial data, prevent fraud, and ensure compliance with strict regulatory standards.
Healthcare and Pharmaceuticals: Secure patient records, clinical data, and research information while maintaining privacy and regulatory compliance.
Government and Public Sector: Safeguard national data, citizen information, and critical digital infrastructure from cyber threats.
IT Services and Consulting: Design, implement, and manage security solutions for multiple clients across industries.
E-commerce and Retail: Protect customer payment data, online transactions, and digital platforms from breaches and cybercrime.
Manufacturing and Logistics: Secure operational systems, supply chain data, and connected industrial technologies from disruption.
Education and Research: Protect academic records, intellectual property, and research data from unauthorized access and misuse.
Every industry that handles data needs security, and that’s nearly all of them.
9. Why Waiting Can Cost You More Than You Think
Here’s something many professionals realize too late:
Security roles are filling fast, and expectations are rising.
What was once “optional knowledge” is now mandatory expertise. Each year you delay:
-
Competition increases
-
Certification becomes the baseline
-
Opportunities go to those already prepared
Starting now puts you ahead of the curve, not scrambling to catch up.
The digital world isn’t slowing down, and neither are the risks that come with it. Information security professionals are no longer just protecting systems; they’re protecting trust, careers, and entire organizations.
Choosing to upskill today means positioning yourself for opportunities others will only realize tomorrow. An Information Security Certificate is your chance to step into a role that offers purpose, stability, and long-term growth.
With the IIFIS Information Security Certificate, you gain structured learning, industry relevance, and the confidence to move forward in a field that rewards preparation.
The future belongs to those who are ready now is the time to become one of them.










